Creating Tests – As long as they are automated
I have been often asked about testing, how something could be tested automatically, how something could be tested at all. Especially if there is/was no testing framework. My answer has been always the same:
It doesn’t matter. As long the tests are autmated.
Testing frameworks have been created over time. They have not been there from the beginning. Eventually, there is no test framework for your problem yet. However, this does not mean you can’t test.
An error was reported in my EIP-PlantUML side project. After some analysis, I figured out it was caused by a syntax issue within a string in a definition file. The problem here, you see the particular error only once the result has been rendered as an image. How to test this?
I simply wrote a Bash script checking the definitions instead. That’s all. It passes with the exit code 0 or 1 if the test fails. That way I will be able to integrate it in a test suite later one ,even if I don’t know how this will look right now.
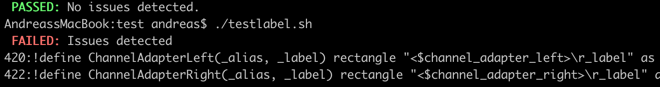
The test script itself is rather simple using grep in a shell script.
#!/bin/bashRed=$'\e[1;31m'Green=$'\e[1;32m'Clear=$'\e[0m'count=$(grep 'r_label' -c ../EIP_Elements.puml)if [ "$count" -eq "0" ] ; then echo "$Green PASSED:$Clear No issues detected." exit 0else echo "$Red FAILED:$Clear Issues detected." grep 'r_label' -n ../EIP_Elements.puml exit 1fi