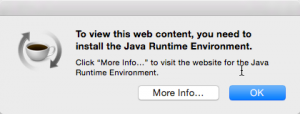
For a couple of weeks I now this really annoying message during the start up of my Yosemite installation.
To view this web content, you need to install the Java Runtime Environment.
If I do follow the instructions of the pop up, I usually land on the Java site.
 As I develop on a regular base, I have the latest version of Java already installed (right no it should be version 8u25). Therefore, nothing to do.
As I develop on a regular base, I have the latest version of Java already installed (right no it should be version 8u25). Therefore, nothing to do.
I case you thought of installing Apple’s Java version for Mac. That’s IMHO not the way to solve the issue. You might cure the symptoms, however, you will not fix the root cause for this issue.
To get rid of the message, you need the find the root cause. In my case it was the attempt to try Facebook’s video chat some weeks ago. That was the only one installation I performed since I receive this message. Even though, I disabled the add-on in Firefeox, the message kept showing at start up.
To get finally rid of the message head straight to the terminal and enter
launchctl list
In case you wonder that launchctl does, check the manpage which says
launchctl interfaces with launchd to load, unload daemons/agents and generally control launchd. launchctl supports taking subcommands on the command line, interactively or even redirected from standard input. These commands can be stored in $HOME/.launchd.conf or /etc/launchd.conf to be read at the time launchd starts.
Anyway, you shot not get a list of off all jobs loaded into launchd. There ckeck if you can find com.facebook.videochat.{username}.updater in this list. Wondering what this is? It’s some kind of Facebook-collects-your-data thing. Honestly, I don’t want to know much more about what it does, I just want to get rid of it.
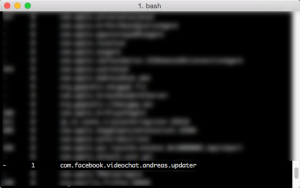
Check out
ls ~/Library/LaunchAgents/ | grep facebook
You should get something like com.facebook.videochat.{username}.plist.
Now run
launchctl unload ~/Library/LaunchAgents/com.facebook.videochat.{username}.plist
followed by
launchctl remove ~/Library/LaunchAgents/com.facebook.videochat.{username}.plist
You might want to run the following command instead
launchctl remove com.facebook.videochat.{username}.updater
You now can delete the property list file
rm ~/Library/LaunchAgents/com.facebook.videochat.{username}.plist
Now check for the FacebookUpdate application via
ls ~/Library/Internet\ Plug-Ins/ | grep Facebook
Again, you should fine something like FacebookVideoCalling.bundle. Send it to /dev/null via
rm ~/Library/Internet\ Plug-Ins/FacebookVideoCalling.bundle
Now there still something to get rid of by calling
rm -R ~/Library/Application\ Support/Facebook/
Et voiá, your are done. The cause for the message should be gone by now.
To get rid of the JAR file itself use Spotlight to looking for FacebookVideoCalling. You should find something like FacebookVideoCalling_v1.6.jar. Use Finder then to get rid of it.
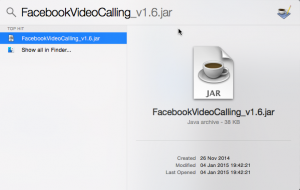 That is, by the way, the only thing Facebook suggest to uninstall the videochat. Not only, the sort of infect you with the above updater, they also do not provide useful information for uninstalling the stuff.
That is, by the way, the only thing Facebook suggest to uninstall the videochat. Not only, the sort of infect you with the above updater, they also do not provide useful information for uninstalling the stuff.
The fact, Facebook’s add-on installed this nasty updater is quite annoying. Adding a job to the launchd for an Firefox add-on is quite questionable. Even more annoying that this one slipped through the cracks.